Choose the best of both Cloud Services and
Web3 - Decentralization
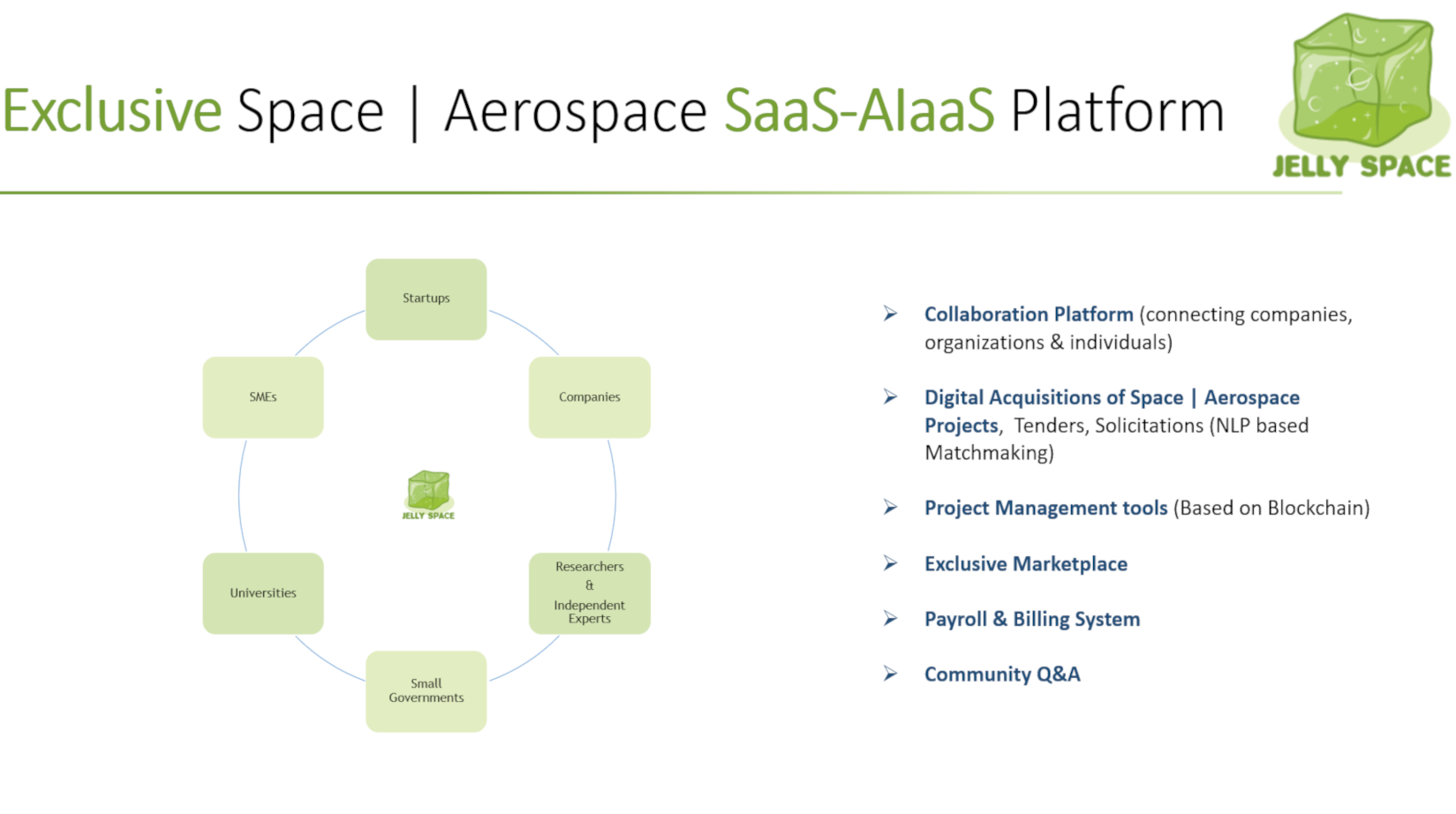
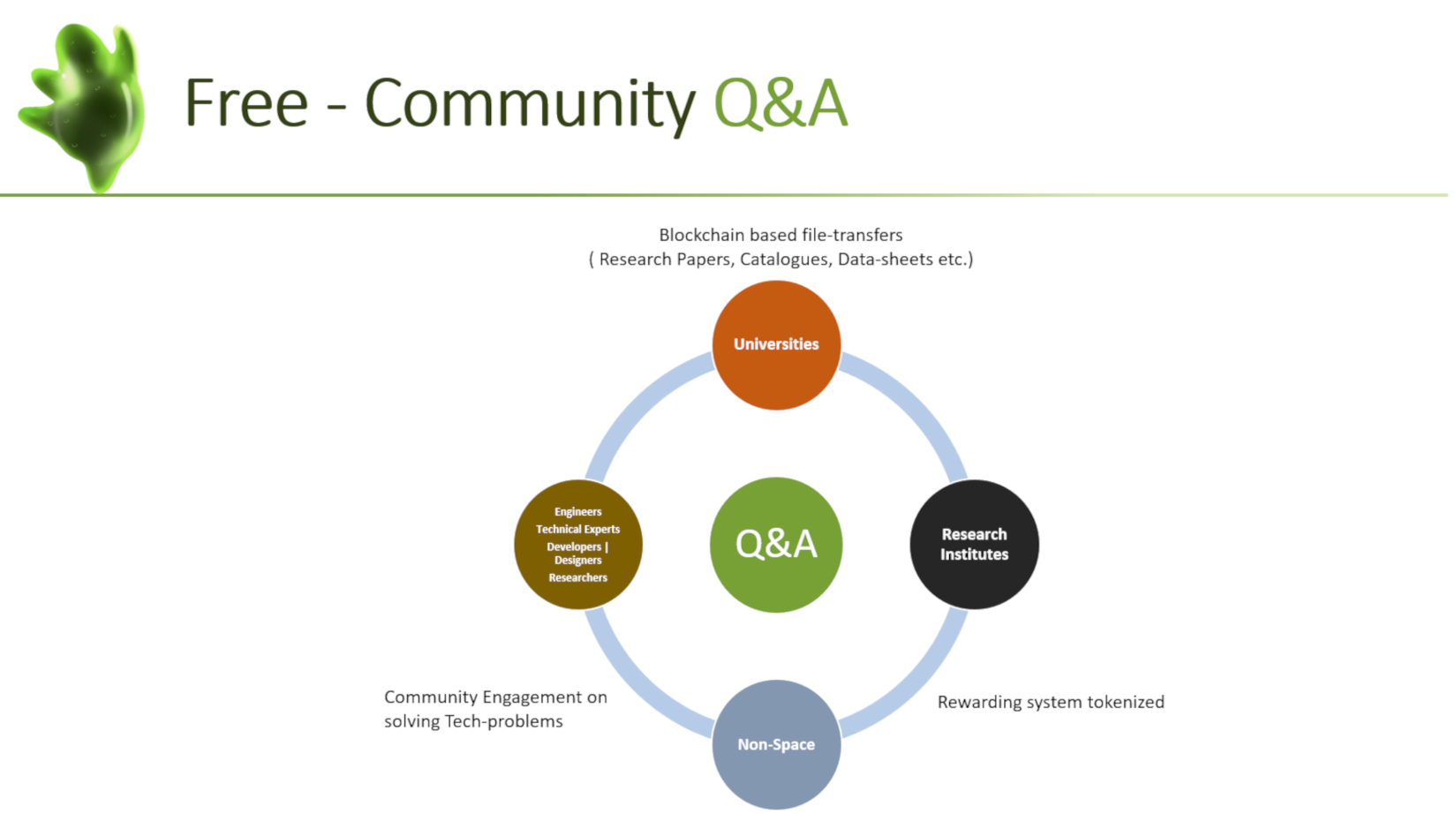
JELLYSPACE understands the complexity of security and discretion required in the Space and Aerospace industry for the Intellectual property (IP) management, i.e., whether it be your designs, catalogues or even conversations.
Our cloud SaaS portal already has you covered with
- CMMC 2.0
- NIST 800-171
We are currently working on bringing ENISA, CMMC 3.0 & FedRAMP Compliance. Moreover, for the EU-Region we are fully GDPR compliant.
What does it mean to get involved and move along with the evolution of Blockchain and its Cybersecurity mechanisms?
Decentralized architectures offer essential data integrity benefits including wide distribution across geographies for innovative disaster resilience, as well as resistance to ransomware and bit rot. An edge-based security model
combined
with delegated proof of stake authorization provides flexible and secure access management capabilities—meaning only you and those you designate have access to your data.
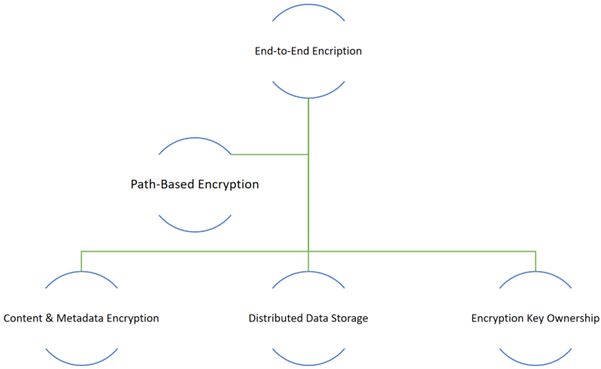
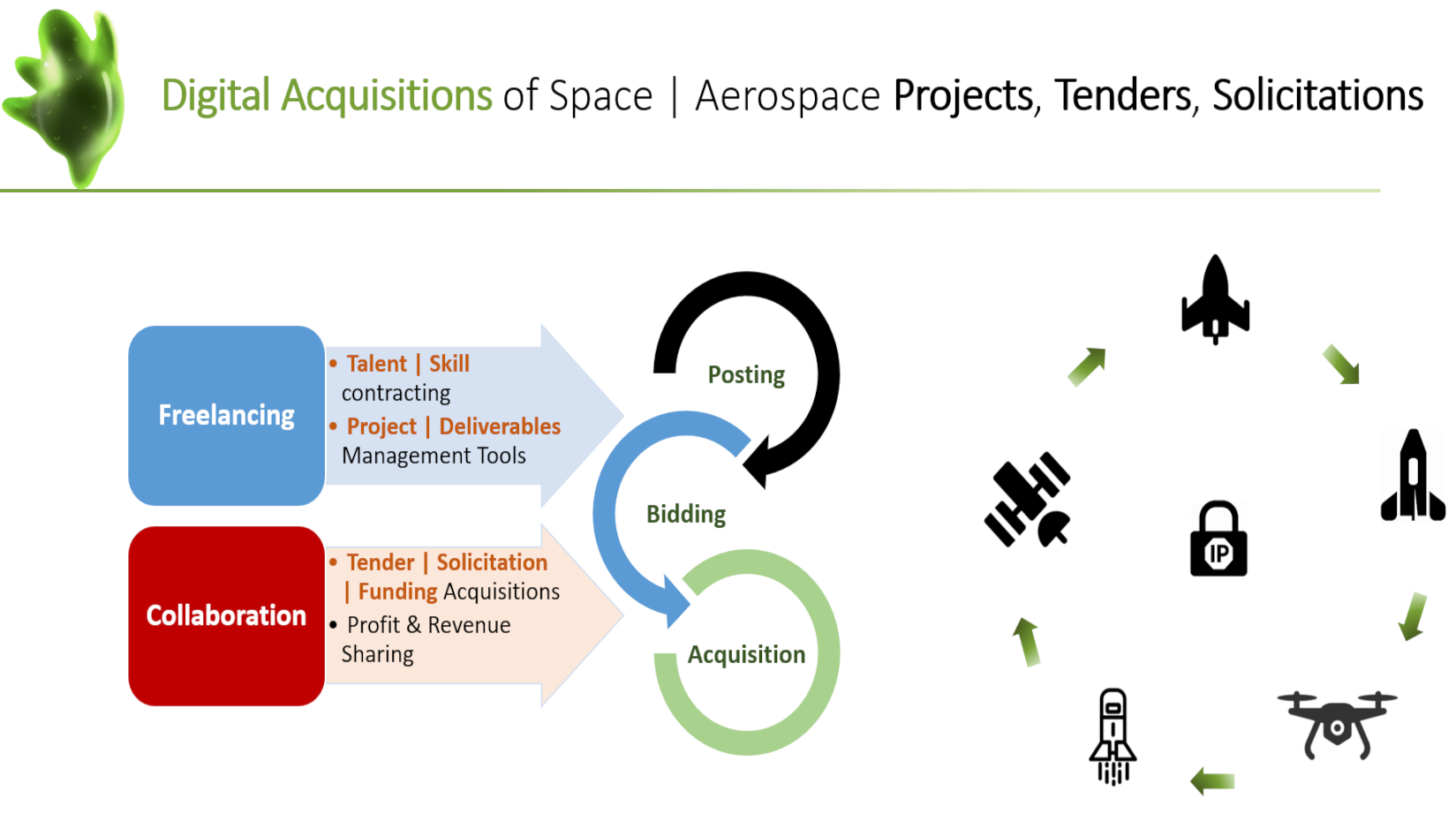
With our Blockchain based security mechanisms and workflow:
- Only End-to-End Encrypted users have access to data.
- Separately encrypted path between sender and recipient is maintained through out.
- Encrypted Metadata & File segments, allow you alone to know what is stored. Even JELLYSPACE will not know about your data & files.
- Encrypted distributed file segments stored and retrieved from multiple geographic locations, avoid Single Point of Failure (SPOF).
- Complete ownership of Encryption keys and data.
- GDPR Compliant Blockchain for EU users
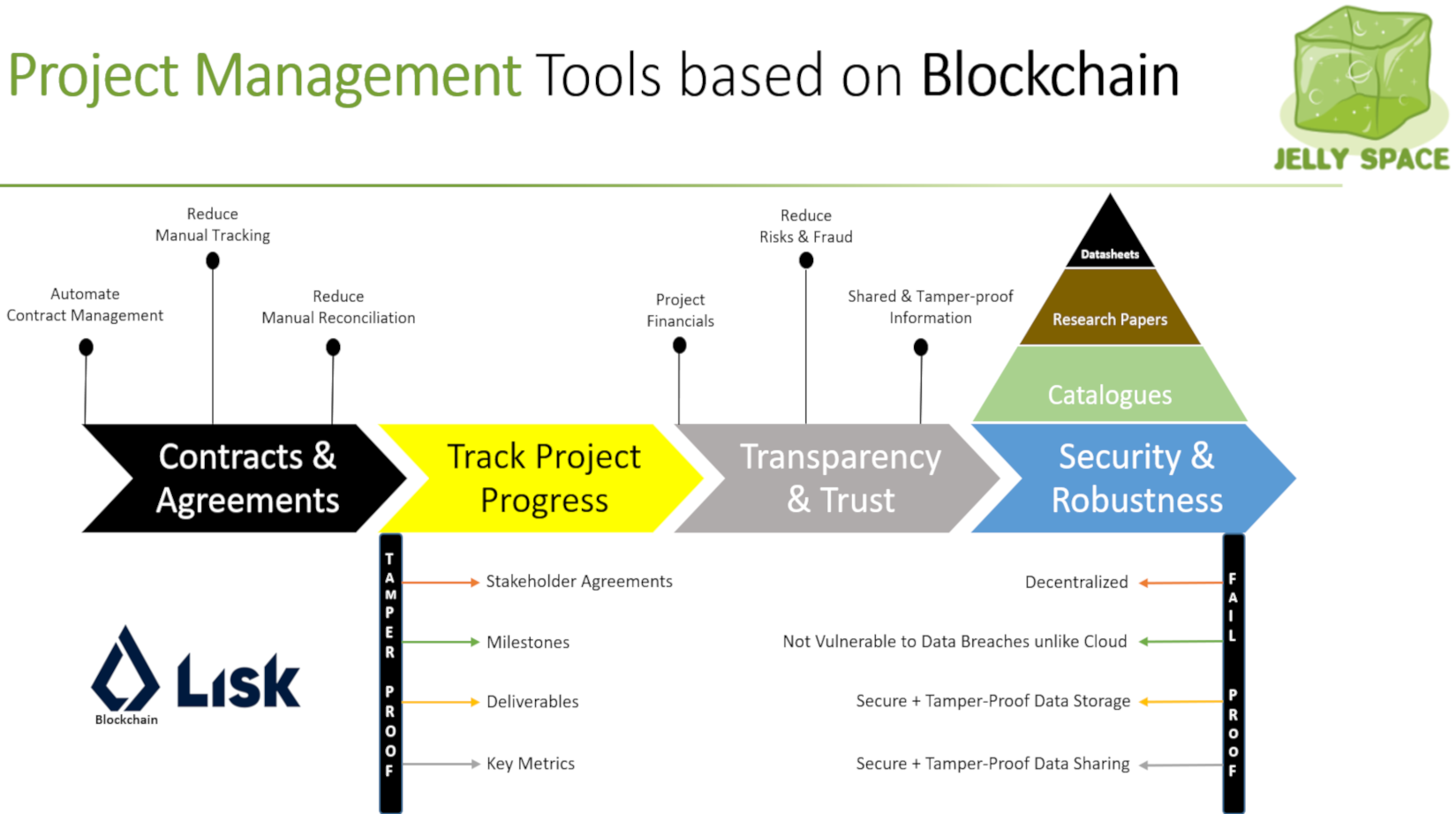
Thus, you can choose to take advantage of either or both the Cloud and Web-3 Technologies based state-of-the-art infrastructure that we are currently developing. We use the latest research based cutting-edge mechanisms from both these worlds. You can further read our blog on our partnership with Lisk Blockchain here.
JELLYSPACE touch base with LISK
Blockchain technologies are evolving and JELLYSPACE intends to leverage and be a catalyst in this process by bringing it to the New Space and Aerospace Industry. Living beings occupy and control a specific time and space, they cannot be blended or averaged as they are part of a biological ledger inscribed through time in their DNA codes which cannot be reversed by outside power. Our properties and transactions compose an immutable ledger bound in time with every entry in the cryptocosmic ledger getting timestamped. Similarly, Intellectual Property (IP) is the DNA of an organization, and its security cannot be retrofitted, patched, or improvised by external structures other than the owner and its parties involved.
As Gilder’s laws of Cryptocosm state that secure positions are decentralized ones just as human minds and DNA code are decentralized. [1] Asymmetric codes in decentralization reproduce the biological asymmetry i.e., data coded by a public key can be decrypted only by a private key, but the private key cannot be calculated from the public key. Innovatively asymmetric codes that are prohibitively difficult to break but easy to verify keep the power in the hands of the IP owner rather than outside entities. Private keys are secure, and they cannot be blended or changed just like our DNA that cannot be changed or blended. They can be held by individuals and enforce property rights and identities. Through digital signatures utilizing private and public keys to encrypt and decrypt data a high level of safety is achieved. This also ensures that a human interpreter is present on both the ends of a transaction and thus making security meaningful. The owner of a Private Key (ID) can always respond to a challenge by proving ownership of the identity of a blockchain and its contents. Thus, in response to any government claims and charges, the owner of the Private Key can prove his/her work and record. The owner of the IP can always prove title to an item of property defined by a public key on a digital ledger.
What does this all mean?
Simply your data and files are yours and the power to share it with another entity or organization remains in your hands. There is an easy way of determining proof of theft or crime through digital signatures and footprints. Any
other
organization cannot claim your intellectual property and data to be theirs.
Meet our Team ↗
References:
[1] Life After Google: The Fall of Big Data and the Rise of the Blockchain Economy - George Gilder